SaaS is characterized by a rapid evolution of product capabilities providing new features and benefits to the customer. The success of any SaaS business is critically dependent on its ability to provide their service with high reliability, security, privacy, and performance. In the “as-a-Service” world, the software vendor must provide these services to meet the customer’s functional needs, but also meet their increasingly demanding and complex global regulatory requirements.
The requirements of running a SaaS operation are constantly changing. New security threats emerge on a daily basis, and governmental standards frequently make radical shifts. Additionally, SaaS systems must integrate and interoperate with other SaaS offerings and data sources.
Running SaaS operation must be done at an economical cost while meeting all the stringent requirements. The economic constraints on running a SaaS operation are described in the Cloud Strategies’ article, The Imperative to Reduce the Cost of SaaS Service. While cost reduction is key, the SaaS customer’s requirements must be met through most SaaS development and SaaS operations best practices.
The Process of Building a World-Class SaaS Operation
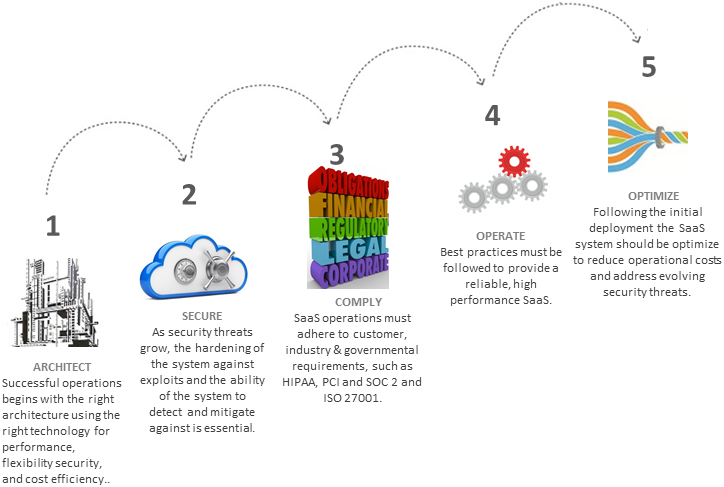
Steps to Building a World-class SaaS Operation
The process of building a SaaS operation includes these five major stages described in each section of this article:
As SaaS operations are optimized through adopting best practices and the use of new technology, the quality and efficiency will continuously improve.
Components of Successful SaaS Operations
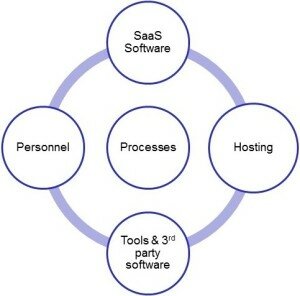 Efficient SaaS service delivery requires the effective collaboration between all constituents in the SaaS operation.
Efficient SaaS service delivery requires the effective collaboration between all constituents in the SaaS operation.
DevOps is the combination of the SaaS software development and the SaaS operational personnel to maximize the predictability, efficiency, security, and maintainability of the SaaS operations.
The Service Delivery provider can be another key component on SaaS operations. The hosting provider can provide all the essential hosting components that are required by the SaaS application to be deployed including Public, Private, and Hybrid Clouds. The Hosting provider should possess the expertise in areas such as security and compliance, and can provide services such as patch management.
The SaaS operations are dependent on third party tools and applications such as system monitoring, Intrusion Detection or Intrusion Prevention Systems (IDS/IPS), databases, and integration tools. These tools, systems, and data sources provide both an opportunity for superior operations, but also a risk of system failure, performance problems, and security issues.
SAAS OPERATIONS ARCHITECTURE
When building a SaaS operation, the first step is to develop the architecture which meets the system requirements.
Requirements for SaaS Operations Architectures
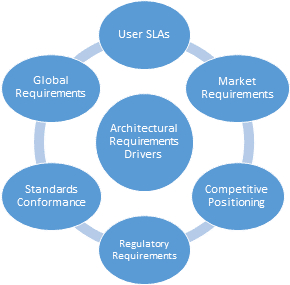 The architecture needs to start from the requirements of the client the offering is created to serve. The specific customer requirements are expressed formally in the Service Level Agreement (SLA) and are also influenced by the requirements of the market, competition, and regulatory constraints.
The architecture needs to start from the requirements of the client the offering is created to serve. The specific customer requirements are expressed formally in the Service Level Agreement (SLA) and are also influenced by the requirements of the market, competition, and regulatory constraints.
This architecture should start with a collaborative effort between the development and the operations teams. Companies such as Netflix have a single team that is responsible for both the product development and operations. Most SaaS companies have separate development and operations organizations, so collaboration between these two departments is imperative to deliver a successful service. The more tightly linked development and SaaS operations are, the greater the potential for reducing the operational costs by making the SaaS service more efficient through process improvements and automation.
Software Ramifications on SaaS Operations
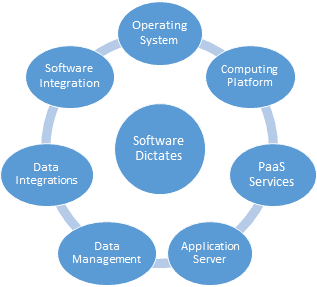 When delivering Software as a Service, operations must be optimized as described in the article Software Development for SaaS is Different. SaaS software requirements will impact the selection of mode of Service Delivery, the components and the configuration of the hardware and software infrastructure.
When delivering Software as a Service, operations must be optimized as described in the article Software Development for SaaS is Different. SaaS software requirements will impact the selection of mode of Service Delivery, the components and the configuration of the hardware and software infrastructure.
Resource Isolation and Multi-tenancy
Efficient SaaS operations are always architected for multi-tenancy unless high security constraints prohibit the use of multi-tenancy. SaaS software for each tenant can share the same:
- Physical hardware
- Virtual machines
- Processes
- Database
- Tables within a database
The issue is the degree of isolation required for security, and the complexity of the SaaS product. Basic SaaS solutions can simply be a subscription pricing model built on top a hosted platform typically by a Managed Service Provider (MSP). While the operational costs are high, it allows software ISVs to enter the SaaS market with a subscription product. See the Cloud Strategies’ article, The Software Vendor’s Transformation to SaaS. With greater sharing of resources through multi-tenant enablement and management, the hosting and administrative costs will decline. Multi-tenancy should be a component of any world-class SaaS software architecture.
Data Management Software
The data management platforms used by the SaaS platform will have significant effect on operations. Databases must be monitored for storage use, optimization and their performance. NoSQL databases such as MongoDB, Cassandra or Google’s Big Table as well as big data platforms such as Hadoop, have major implications for the SaaS operations.
Software and Data Integration
Integrations with other software offerings and data sources can create significant SaaS operational impacts. These integrations are done directly between software components using RESTful APIs, SOAP interfaces, or less sophisticated techniques such as “screen scraping” or .csv imports. Third party Enterprise Service Bus tools such as MuleSoft or Cast Iron, or app store interfaces such as Salesforce’s AppExchange or NetSuite’s SuiteTalk can also be used to integrate SaaS offerings to third party programs and data sources. Screen scraping is still a surprisingly widely used “integration” technique, but is not scalable and prone to breaking after interface changes. API integrations can break when they are depreciated or their behaviors are changed without notice. Different interfaces have different levels of efficiency and resiliency impacting their overall SaaS operations.
SaaS Operational Requirements
SaaS solutions requirements include performance, scalability, disaster recovery and business continuity.
The SaaS operational service delivery system must be architected to adapt to rapid shifts in demand, by adding resources in real-time. The scaling requirements are highly dependent on the nature of the SaaS product. For example, e-commerce applications may have large spikes during holiday seasons. Other systems may have more predictable demands and not require as much scalability. The SaaS operations structure must be architected to handle peak loads and be tested to ensure the systems can met these loads. Private Clouds with fixed resources may need to implement “cloud bursting” to enable a shift of load to public clouds during these peak periods. New technologies like Solid State Disks (SSD) can profoundly impact the SaaS architecture to realize much higher performance.
Architectural patterns for horizontal scalability includes sharding of resources to partition the workloads. Sharding entails additional complexity to ensure that the scaling is transparent to the user.
Redundancy, data, fail-over, and fault tolerance are all critical considerations of a robust SaaS architecture. SaaS systems should provide fault tolerance to accommodate failures in any given component that require a transparent handoff to other computing resources in whatever geography is being supported. This requires sufficient network bandwidth and the synchronization of data at multiple locations to make the system highly resilient.
Hosting Provider Selections and Configuration
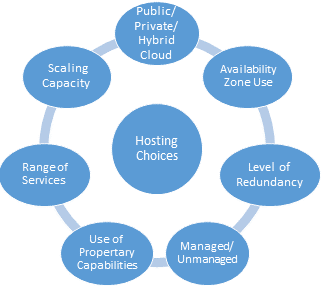 Many of these architectural choices, including security and compliance issues, which are discussed later in this Guidebook, will influence the choice of the service delivery provider.
Many of these architectural choices, including security and compliance issues, which are discussed later in this Guidebook, will influence the choice of the service delivery provider.
The decision to use a Public, Private, Hybrid cloud, or even a co-location environment dictates many other SaaS operations architectural decisions. The choice among these options will depend on the security, performance, and flexibility requirements of the overall SaaS operational architecture.
The choice of computing environments based platforms on such OpenStack, Microsoft Azure, Google Cloud Platform, Amazon Web Services (AWS), or another proprietary platform can dramatically impact the SaaS operational architecture. SaaS operations should be certain to optimize for the architectural foundations of the proper software platform.
There is also a concern about provider “lock-in” when using proprietary features of these platforms and their associated PaaS (Platform as a Service) capabilities. Many SaaS providers will only use capabilities and interfaces that are operational across multiple platforms.
Service delivery providers differ substantially in their geographic reach and number of availability zones they offer. A highly robust SaaS offering must have its data replicated in multiple regions to protect against both system failures in one location and regional disasters which impact the ability to operate in a single geographic region.
Service Delivery providers can often provide valuable architectural and configuration guidance for constructing the hosted environment, and a trusted partner can provide essential insights.
SECURING THE SAAS SYSTEM
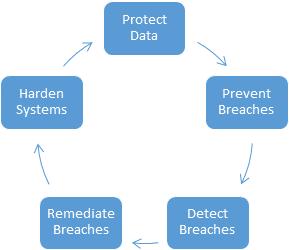 SaaS and internet-based systems have an inherently more difficult task of protecting their operations due to the public access to their software. Legacy client/server systems often restrict their access to the software behind the corporate firewall or through Virtual Private Networks (VPNs). Modern systems have world-wide access providing many more points of attack which must be protected.
SaaS and internet-based systems have an inherently more difficult task of protecting their operations due to the public access to their software. Legacy client/server systems often restrict their access to the software behind the corporate firewall or through Virtual Private Networks (VPNs). Modern systems have world-wide access providing many more points of attack which must be protected.
Providing a secure SaaS platform is often the primary goal of SaaS operations. In many applications, having the system breached is worse than not having the system operational.
Securing SaaS operations requires a collaborative effort between the development, SaaS operation’s personnel as well as the hosting provider. Beyond the actions of these groups, it is important to have external resources which are auditing and testing the SaaS operational defenses just as the “malicious actors” are doing.
Categories of SaaS Security Attacks
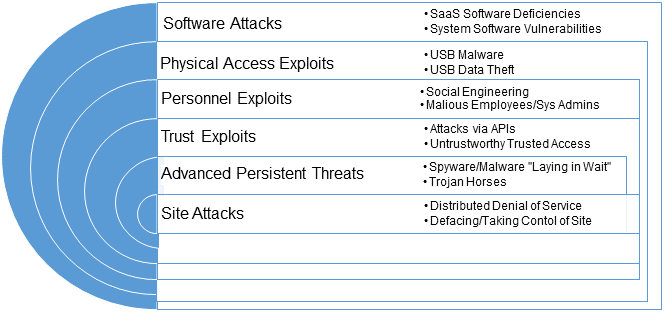 Malware in SaaS systems have many different methods of targeting software or operational weaknesses.
Malware in SaaS systems have many different methods of targeting software or operational weaknesses.
Software Attacks
Flaws in the SaaS software may allow the introduction of viruses by executing malware that is introduced into the system through browser, mobile, or API input which the system is “tricked” into executing with high security privileges of the SaaS software. SQL Injection and Cross Site Scripting are the two most common methods of comprising the software.
Vulnerabilities in the operating system and other third-party software have enabled malicious actors to gain access to portions of SaaS data (Heartbleed) or take control of the SaaS system (Shellshock).
Physical Access Exploits
Physical access to the computer servers or any computer which has access to secure data opens the ability to both introduce viruses into the system (Stuxnet – Iran) or remove sensitive data from the system (Snowden – CIA, Bradley Manning – US Army).
Personnel Exploits
Humans with access to secure systems are a high risk of compromising systems. System administrators (such as Edward Snowden) with access to the unencrypted data and systems should be limited.
Access to the SaaS systems by unauthorized users can be enabled through social engineering to determine security credentials of legitimate users by locating their authentication information through social sources. Additionally when users use the identical password on multiple systems, a password which is revealed on one compromised system may give access to another system using the same password for the user.
Trust Exploits
Both software and users with high trust levels can be exploited by malware. SaaS system software has a presumed high level of trust which can be exploited as described in the Software Attacks discussion above. Multiple software systems can share the same security and firewalls letting access to one system expose data from a second, more secure system.
A particular risk with SaaS is the pervasive use of APIs which, if not secured, can be used to exploit the system. All access points to the system must be assumed to be gateways for the introduction of malware (Target credit card database breached through HVAC software).
Malware may be introduced into computers, which are authorized to access the SaaS system, and then access the SaaS system through those infected computers with the credentials of the authorized users (China hacks into New York Times).
Advanced Persistent Threats
A dangerous forum of malware is the Advanced Persistent Threat (APT) which is introduced into the system by a method described above, but lays dominant until called to action. This type of threat may be used to slowly and surreptitiously transmit sensitive data to unauthorized external systems with minimal evidence of the actions.
Site Attacks
Aside from malware being used to gain access to SaaS systems and their data, the malware may directly act to prevent the SaaS system from functioning through a Distributed Denial of Service, DDoS (Sony DDoS).
A lack of security in accessing a company’s web site may allow the hacker to “take over” the website to deface and prevent access to the SaaS system.
Malware
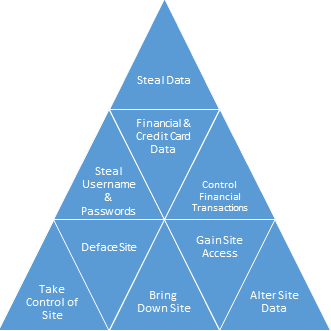 Malware authors are generally divided into these categories: stealing data, altering data, installing malware, taking control of the system or transaction on the systems, and taking down SaaS operations.
Malware authors are generally divided into these categories: stealing data, altering data, installing malware, taking control of the system or transaction on the systems, and taking down SaaS operations.
The most publicized security breaches have been in the theft of credit card data, and user name and passwords. User names and passwords can be used to break into individual accounts to initiate unauthorized activity on the user’s behalf, presumably with the intent of financial gain or exploitation of private information (Apple celebrity photo leak).
Other exploits involve altering data on the SaaS system (Students change grades), encrypting the data requiring payment for access (Ransomware), stealing credit card information for resale (Russian Hackers) or disrupting the system operations (DDoS).
SaaS Operational Countermeasures
SaaS Operations must have multiple approaches of offense and defense to protect against security breaches. SaaS operations must control the access to the system and its data, hardening the vendor and system software from exploits, and creates the processes to defend against current and future attacks.
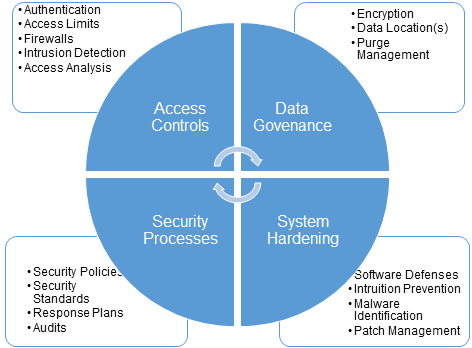
Access Controls
The limits on access to the SaaS system is fundamental to security. That process starts with robust authentication ideally using industry standard authentication and leveraging off of the customer’s Single Sign-On (SSO) tools. The logon credentials must be encrypted, salted, and required to be sufficiently complex to avoid dictionary based attacks in order to avoid the frequent occurrence of stolen password files, which have then been used to attack other systems (LinkedIn).
It is necessary to restrict the access to the system and the data to the minimum set of system administration personnel. Reducing the total number of system administrators with meaningful system access through automation can decrease the likelihood of security breaches.
The next line of defense against malicious attacks is both through conventional (network layer analysis) and application (application layer analysis) firewalls.
Intrusion Detection Systems must be used to detect system breaches as soon as possible. Additionally, SaaS vendors with high security applications should monitor the data usage access to detect patterns that indicate a potential theft of data.
Data Governance
Access and control of the data are the top priorities in securing SaaS systems. For secure systems, the data should be encrypted both when stored (at rest) and while being sent of a network (in motion). The use of encrypted web access through SSL secured communication (https) is the standard for all web sites.
SaaS data is often replicated in multiple locations for resiliency, performance, and disaster recovery. It is essential the data is encrypted in each location, and the key management is protected so only the end user, not the SaaS provider can have unencrypted access to the data wherever possible.
Data should also be purged or the encryption keys destroyed when access is no longer required for high security applications.
System Hardening
SaaS systems should continually be enhanced to ensure the software, the operating system, and the computing environment are as secure as possible against attacks.
Static code analysis should be done on the SaaS software to identify areas of security weaknesses and flaws. Dynamic analysis of running code is also required to test for attacks on the SaaS software.
IDS and IPS should be in place to identify and defend against attacks. Many alternates are available to defend against DDoS attacks by intercepting and removing the attack traffic.
It is also imperative to have aggressive patch management systems in place to quickly patch vulnerable software against Zero-day attacks.
Security Processes
The defense against threats is a never ending process that must be in place to continue to harden the system’s defenses and respond quickly to new attacks.
Security policies should be put in place which specify the standards to be followed, the ongoing steps to be taken to keep the system secure, and the actions to be taken in the event of an attack. Specific industry standards (such as PCI DSS for e-commerce) provide a minimum set of criteria for secure operations.
Security processes should be constructed with the assistance of security experts outside of the SaaS vendor’s firm. Few SaaS vendors have the expertise or breath of experience of external resources required to harden their system against all potential threats.
Finally, SaaS security should be audited and tested by an outside group. It is impossible for the same group to both build the security mechanisms and test them thoroughly.
ENSURING SAAS COMPLIANCE
Compliance is becoming a central element of running a SaaS service delivery operation. The penalties for not meeting compliance requirements can threaten the viability of any SaaS company.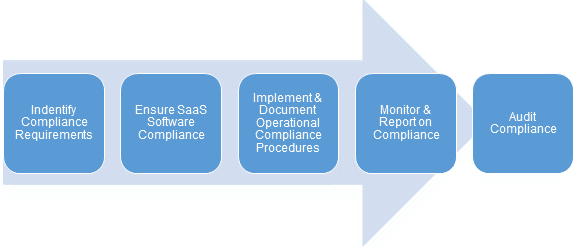 The first step to having a compliant SaaS operation is to identify the compliance requirements for the business. Compliance dictates many of the operational procedures that are necessary to run any type of SaaS business. These procedures must be created, documented, and adhered to. Once these procedures are in place, they must be monitored and the system continually assessed to verify it meets all the compliance requirements, typically by a third party auditor. There are major impacts if the SaaS company is found not to conform to compliance laws and standards.
The first step to having a compliant SaaS operation is to identify the compliance requirements for the business. Compliance dictates many of the operational procedures that are necessary to run any type of SaaS business. These procedures must be created, documented, and adhered to. Once these procedures are in place, they must be monitored and the system continually assessed to verify it meets all the compliance requirements, typically by a third party auditor. There are major impacts if the SaaS company is found not to conform to compliance laws and standards.
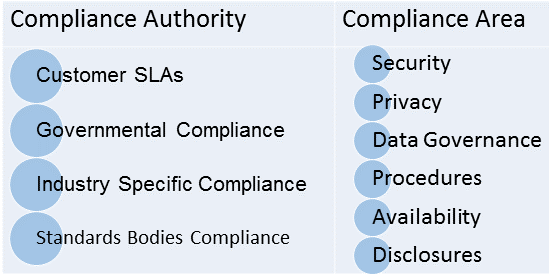
There are many different authorities (including customers) that have compliance requirements each overlapping in the area of compliance in which their standards apply:
Compliance Authorities
Customer SLAs
For SaaS systems to be useful, they must meet the function requirements of their customers and offer assurances of the quality of how they deliver these services. All SaaS contracts include warrantee agreement that may limit the rights of customers more than give rights to customers.
Larger companies selling to businesses have SLA such as the NetSuite SLA Commitment. These agreements may include guarantees for uptime, performance levels, response time, disaster recovery assurances, privacy, security, and even in some cases, specific business results. These SLA’s explicitly specify the remedies and penalties for failing to meet the standards and the remedies the SaaS company commits to take.
Governmental Compliance
Compliance with governmental regulations are the greatest risk and complexity for the SaaS vendor. Failure to comply can result in the failure of a company or the imprisonment of the executives.
Sarbanes–Oxley created a massive amount of new regulation, particularly in specifying the processing of information, the roles of people involved (particularly in segregation of duties), and the reporting requirements.
Governments are creating new regulations that apply broadly to SaaS and other companies for disclosure of security breaches, particularly of credit card or user/password information.
The recent trend is to have many more unique requirements from a single country or a block of countries such as the European Union (EU). In the United States, even some states have their own regulations. These regulations are a greater problem for the SaaS vendor than the software vendor since the SaaS vendor must operate in each region rather than have the customer be responsible for the operation under each jurisdiction. EU regulators are creating increasingly strict regulations on the location of data used in their countries and the privacy protection of their citizens.
Industry Specific Compliance
Governments also create requirements of specific industries such as medical and defense, regulating security and privacy through laws such as HIPAA. These regulations are extremely complex and have severe penalties and liabilities for failure to comply with these regulations.
Governments such as the United States may delegate the construction of the specific regulations to an industry organization such as the PCI Security Council for credit card information or the Financial Industry Regulatory Authority (FINRA) for securities transactions which are sanctioned by the U.S. Securities and Exchange Commission. Failure to comply with these regulations can result in both fines and result in a financial exposure due to civil actions taken against losses caused by failure to adhere to these standards.
Standards Bodies Compliance
Standards bodies such as the International Standards Organization, have created broad standards which have been internationally and then endorsed by governmental organizations. For example, ISO 27001 specifies security requirement for IT systems that are applicable globally. These standards bodies become de-facto creators of regulations which SaaS vendors must certify they are compliant to in certain industries.
Compliance Areas
Each compliance authority is a component of most of the regulations created by the compliance authorities – there is overlap and occasionally conflict in these regulations, particularly between different countries. For example, there is a conflict between the US beliefs in free speech versus the EU belief in privacy or the Chinese desire to restrict the information which their citizens may have access to.
Security
Security is a major area of regulation, particularly in defense, financial, and medical applications. SaaS providers must ensure that their information is secure because they may be handling financial transactions or confidential information stored in document management systems so they are compliant.
Attacks against SaaS systems can result in downtime that impacts the availability. SaaS customers require assurances that they will not get malware infections from using the SaaS systems and want contractual remedies if the event the security breaches adversely affect them.
Security Standards such as PCI DSS and ISO 27001 must be accredited by an independent auditor.
A major new concern for all SaaS systems is the access of user data by foreign or domestic governments. This access can take the form of government requests of information held within the SaaS system, or monitoring of customer information without notice. This has driven a massive shift to the encryption of much of the Internet traffic and restrictions in the transfer of data and computing systems outside of country borders (see Data Governance below). Non-US governments are rapidly creating new regulations controlling the use of their citizen’s data.
Privacy
Historically, the privacy rights of individuals has been dictated by the software provider in their “Terms of Service” (TOS) unless covered by a specific regulation generally related to medical and financial data. HIPAA has extensive regulation for patient privacy. HIPAA compliance requires rigorous encryption of patient data, restriction on access, and security processes implemented in the SaaS software.
Privacy regulations are expanding rapidly beyond medical and financial data. The EU has codified the regulations in the “Data Protection Directory” (“Directive 95/46/EC”). Companies are required to give notice when their data is being collected and why, the collection of data requires the user’s consent, the access of the data is restricted, and there must be means to correct inaccurate data. The International Safe Harbor Principals provides a streamlined process for US companies to comply with the European Data Protection Directive. US SaaS companies should take advantage of this simplified, less risky framework for compliance.
Besides Europe, most countries have regulations for the control of Personally Identifiable Information (PII). Disclosure of this information can both provide the risk of fraud through financial information, or disclosure of private information that is prohibited by law in many jurisdictions.
SaaS companies should also consider participating in TRUSTe in which companies “self-certify” that they follow the TRUSTe standards to safely collect and user customer data. The TRUSTe certificate indicates the SaaS company complies with its own privacy statement and the TRUSTe’s program requirements. This helps provide a framework for basic privacy assurance.
SaaS vendors have extensive customer data which allows vendors to understand and benchmark how their customers use the system. It is essential that permission from their SaaS clients to use this data is obtained, and institute procedures specifying how the data will be anonymized to prevent disclosure of confidential customer data.
Data Governance
Data Governance has become a major area of regulatory activity. The data location and security is an exploding area of regulation with the concerns about government spying on citizens in other countries. This is also a major threat to the growth of the SaaS industry.
Many companies with large SaaS offerings such as Apple, Microsoft, Google, and Yahoo are aggressively hardening their data security through encryption throughout their systems, and limiting their ability to access and decrypt their customer’s data.
The specification and testing of this data security is specified in their Data Governance policies and procedures. This governance provides the assurance that the data is protected, and stored in the locations prescribed by the user in compliance with the governmental regulation to protect their citizens.
Data governance is also an area specified in SaaS customer’s SLAs. Users want assurance in where their data is stored, how it is secured, how it is backed up, and how they can access their data independently of the SaaS software.
Procedures
SaaS vendors also must certify that they operate in a manner that follows regulatory procedures. SOX Section 404 – Assessment of internal controls, requires organizations to assess their internal controls, particularly to prevent fraud. The requirements of SOX 404 audit impact the SaaS software that supports these companies.
SaaS operations often are required to comply with SSAE 16/SOC 1, 2, and 3 that measure the control of financial reporting, security, privacy and related controls. These standards and others for different industries are compliance requirements for SaaS vendors serving the industry which the regulations apply.
Additionally, SaaS vendors must often certify as part of the SLA agreement that they follow best industry practices associated with ITIL (Information Technology Infrastructure Library) and other standards. Adherence to IT standards such as ITIL provides customers an indication that the SaaS vendor is following best IT practices. In practice, it is rare to have the ITIL standard committed to for a SaaS vendor, though larger customers with sufficient leverage may request these certifications.
Availability
Availability, performance, and response time for incidents are common requirement of a SaaS organization. Most large SaaS companies provide standard, but limited availability guarantees only deviating from them for their largest customers. The larger SaaS vendors typically provide 99.5% availability guarantees offering a partial credit for future SaaS subscription payments if they fail to meet these standards. These standards generally excluded schedule maintenance down time, and are often computed over a calendar quarter reducing the probability of missing the availability guarantee due to a single incident.
SaaS vendors should also specify their guarantees for the disaster recovery processes. Customers want to be assured no matter what catastrophe occurs, the system and the data can be restored.
Disclosures
An increasing requirement of both governmental regulations and customer demands are for greater operational transparency. Regulators are demanding disclosure of security breaches to aid in the identification of the breaches so other company can harden their defenses. SaaS customers also want to know about any security breaches that could impact their data.
Additionally, customers want to have transparency to the uptime of the SaaS systems they use. Many SaaS companies have relatively low uptime guarantees of around 99.5% (3.6 hours of unscheduled downtime), but have actual results that are much higher than their guaranteed levels. Customers are demanding that their SLAs contain provision that they will be notified about the occurrence and the status of all SaaS downtime. The publication of system status is now widespread by companies such as Amazon AWS http://status.aws.amazon.com/ and Salesforce http://trust.salesforce.com/trust/.
SAAS OPERATIONS
Goals of SaaS Operations
SaaS operations are measured by their ability to meet their key objectives of availability, performance, privacy, compliance and efficiency.
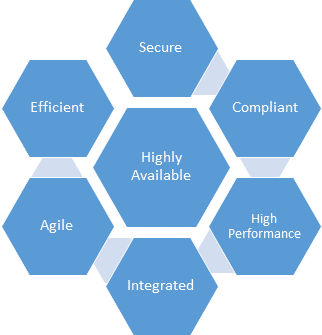
These key SaaS operations attributes include:
Agility
All SaaS operations must be highly agile – capable of rapidly adopting to new requirements to add customers, scale capacity, and adapt to new technologies. SaaS systems must be able to scale instantaneously to momentary demands, and adopt to long term requirements to scale the business efficiently.
Highly Available
A primary component of customer SLAs and expectations are the SaaS systems will be available nearly all the time. When the system fails, it must be assured that no data will be lost, and the operations can be continued regardless of the cause of failure. There will be “business continuity” so that the customer’s business won’t be impacted when problems occur with the SaaS system. This includes both natural disasters and eliminating the potential that any business failure of a SaaS business won’t be an equal disaster for their customers.
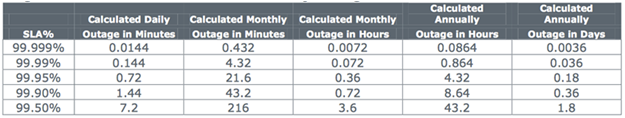
SaaS Outage Time by Percent Availability SLA
High Performance
Expectations are increasing that the SaaS platforms always perform well. SaaS platforms have to address performance issues associated with Internet latencies and users expect a sub-second response for common actions (<250 milliseconds is ideal) and that SaaS applications will load in just a few seconds. Consistent low performance causes customers to abandon the use of applications.
Integrated
SaaS systems are much more likely to be integrated with other off-premises systems than traditional software. When these interfaces change, the SaaS component which depends on that integration will fail. SaaS operations needs to minimize these failures due to integration problems, and respond quickly to these issues.
Efficiency
The cost of SaaS operations varies widely depending on the operational requirements of the SaaS software and the efficiency of the operations. Some SaaS products such as video streaming will be inherently most costly to operate than lower demand SaaS applications, but all SaaS operations can be made more efficient. The median cost of service for public SaaS companies is 17% according to SEC filings.
SaaS companies should drive their costs down to these world-class levels by architecting the applications for maximum efficiency, improving the efficiency of their SaaS operations, and taking advantage of cloud technology trends which are driving downing computing costs for those who take advantage of these cost decreases.
Methods for Achieving SaaS Operational Excellence
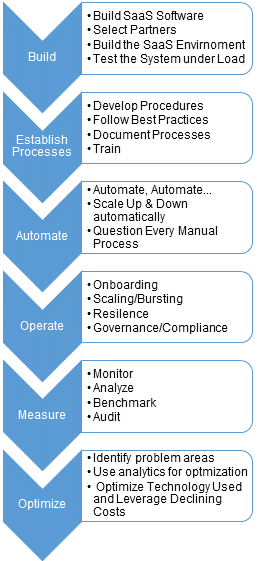 SaaS systems must be managed from their initial setup through their daily operations. Best-in-class operational methods are required from building the system, automating the routine processes, measuring the performance of the operations, and then optimizing those operations.
SaaS systems must be managed from their initial setup through their daily operations. Best-in-class operational methods are required from building the system, automating the routine processes, measuring the performance of the operations, and then optimizing those operations.
Building the SaaS Platform
The SaaS architecture dictates the construction of the platform and the service delivery provider will be selected based on the services they provide. This includes the ability to provide public, private, or hybrid clouds as well as their specific capabilities such as Content Delivery Networks (CDN), managed services, or specialized data storage technology.
The SaaS configuration should be tested in the target environment using load testing tools to ensure both the computing environment and the network will meet the peak demands.
Establish Processes
Once the SaaS operations have been built, the operational processes must be created, tested, and documented. This is required to create a more effective SaaS environment, and is necessary to achieve most compliance objectives.
Creating new processes should leverage off of industry best practices and utilize partners who have the expertise to assist in creating the optimal SaaS environment. This is crucial in areas of security, scalability, and identifying system bottlenecks.
Training is essential for the success of the SaaS operation. Those that have responsibility for the SaaS operation’s success, including the SaaS administrative personnel, support staff and the development staff must be trained in their area of responsibility and particularly know what they must do to quickly resolve operational problems.
Automate
Automation is crucial in SaaS operations for multiple reasons:
- Automated systems can react instantly to changes in the SaaS operations such as changing load conditions or security issues
- Automation can better use analytical tools to identify trends before humans do
- The fewer people administrating the SaaS systems the lower the security risk
- Automation is a key aspect of SaaS operational cost reductions
Automating key processes requires fully understanding those processes and developing an action plan to resolve the system issues.
Many service delivery and PaaS providers provide proprietary automation tools, particularly in scaling and descaling computing resources in response to load changes. Industry standard tools for IT automation such as Puppet and Chef can be used to automate common IT configuration tasks.
Manage
Daily operational tasks of running the SaaS platform can be minimized except to adapt to changing requirements and to leverage technology. Customer on-boarding should be automated to eliminate any manual operations.
The resilience of the system should be continually tested during operation. Tools such as Chaos Monkey, which randomly kill computing resources from production systems are best practices to ensure that the SaaS offering will continue to run reliably whatever the operational environmental problems occur.
Security is an ever-present responsibility of SaaS operations. Intrusions must be continually monitored and information about new security risks from the computing community must be followed closely. It is essential for system security to keep the systems patched and up-to-date to defend against “Zero-day” risks, which were present in the software, but just discovered.
SaaS operations should also be monitoring activity patterns of its software to identify access patterns that could indicate a security breach. They also must look for advanced persistent threats embedded in their systems, which could be sending data outside of the SaaS firewall or lying in wait to expose data or impact the SaaS operation.
Measure
Monitoring the SaaS operations is an essential function. Many tools are available to measure the system, including advanced warning of performance problems or potential system failures. Companies such as Sumo Logic provide SaaS based mining of system logs to provide insights into the system operation to allow SaaS companies to react proactively to problems.
SaaS companies should also benchmark their operations against similar operations to measure their efficiency and leverage the best practices of others.
Audits are a requirement of most SaaS operations.
SAAS OPERATIONS OPTIMIZATION
For SaaS companies to improve their profitability, they must optimize their operation’s performance. The SaaS software should be analyzed during production operation for the “hotspots” that constrain performance and consume unnecessary resources increasing costs.
Licensed software which increases the operational costs of SaaS should be periodically reviewed to ensure it provides the value it costs, and to determine if lower cost alternatives exist. The switching costs to other alternatives may be prohibitive, but the costs of current software should be understood, and knowing the costs of alternatives may allow for better price negotiations with incumbent vendors.
Likewise, service delivery costs should be periodically analyzed. Cloud computing costs are declining regularly — SaaS vendors should be benefiting by these costs reductions to lower their operational costs. SaaS vendors should periodically review their use of public, private, and hybrid systems to look for the lowest cost alternatives which are expandable, and provide the necessary services while meeting their security and compliance requirements.
CONCLUSIONS
Building a world-class SaaS service delivery operation is a challenge. SaaS, as a technology, is a new mode of computing and the best-practices are still being developed.
SaaS companies face operational challenges not previously encountered by their on-premises software predecessors with need to perform their customer’s operational functions while responding to increasing regulatory requirement and a greatly increasing level of malware attacks. SaaS providers encounter new issues in providing their offerings to foreign customers who operate under a different and sometimes conflicting set of laws.
Additionally, it is essential to minimize the cost of the SaaS operations to help drive the profitability. SaaS vendors with significantly higher service delivery costs will have a difficult time achieving profitability and a positive cash flow.
While the challenges are substantial, the SaaS vendor development and operations teams working together with their service delivery providers and partners can create a world-class SaaS platform that will help drive the company’s success.